Two uses for multiple Nebula networks you haven't thought of
(And two you probably have)
You may already know Managed Nebula is a great way to securely connect your computers and devices, wherever they might be located. You may also know that you can set up roles and firewall rules within your private network to control how those machines can communicate with each other, and that you can create tags that carry configuration, making it easy to manage large networks. But did you know that you can also reuse those roles, firewall rules, and tags across multiple private networks all in the same Managed Nebula account?
Multiple Managed Nebula networks
We recently introduced the ability to do just that. The roles, tags, firewall rules, and API keys you’ve set up in your account can be reused across networks, but the networks themselves remain separate. Hosts on one network cannot communicate with those on any other network, enforced by nebula certificate authentication. This lets us use them in some powerful ways.
Separate networks per environment
If you manage infrastructure for a company or SAAS project, you may immediately think of one of the most obvious uses for multiple networks: separate development and production environments. Indeed, having one Managed Nebula network for your development/test/staging environment and another network for your production environment is an excellent way to improve the security and reliability of your most important operations. And since tags, roles, and firewall rules are shared between networks, you can be sure that your test network mimics your production network as closely as you want.
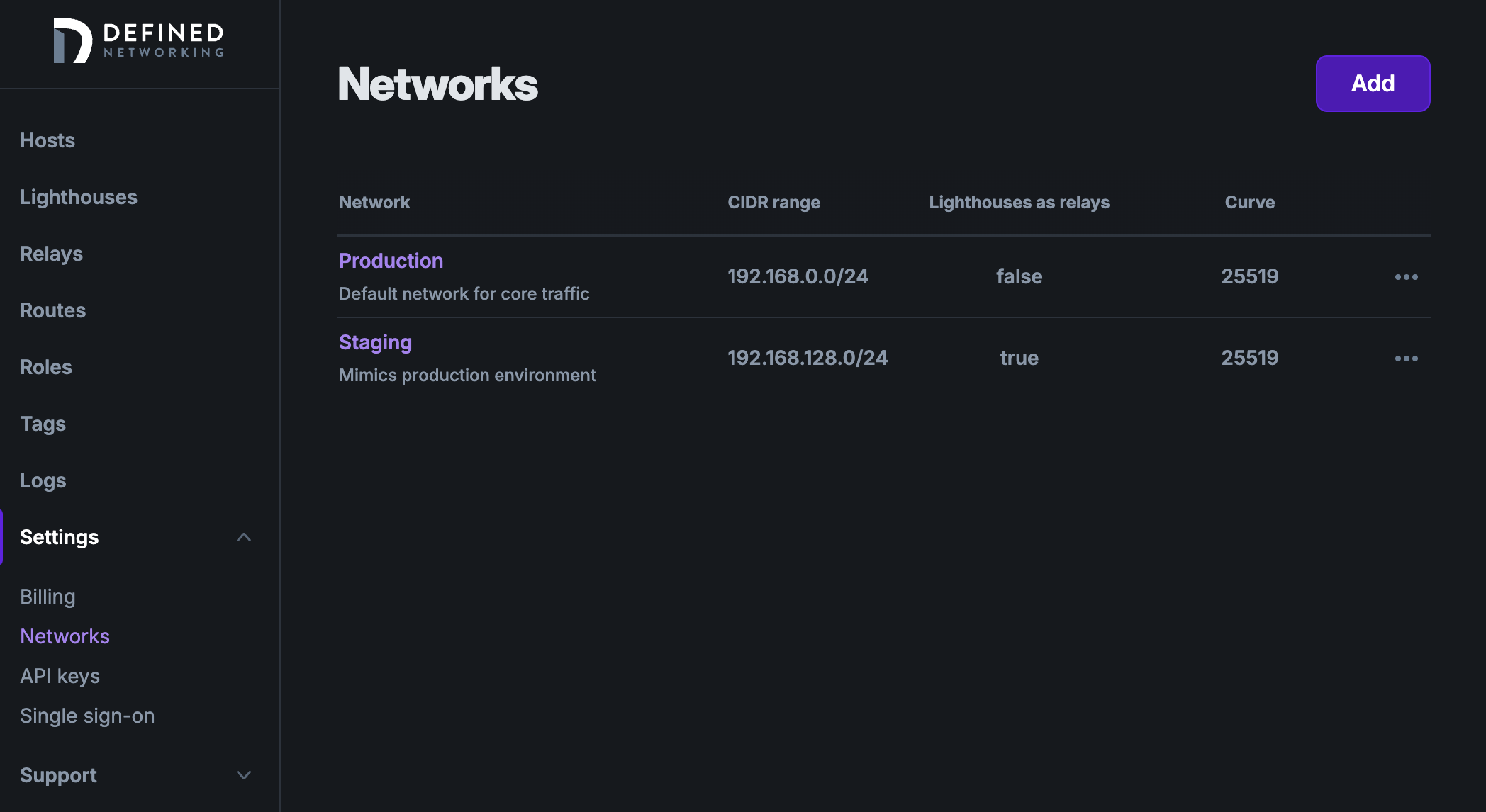
Migrate to a new Nebula IP address range
Another popular use for multiple networks is to migrate from one range of IP addresses to another. In fact, this is a main reason why we built the feature in the first place. Previously, users needed to delete their entire account and start over in order to change their network CIDR range. Now, it’s possible to create a new network with the desired addresses and move hosts over to it. We have a full guide on how to accomplish this, including a zero-downtime method which involves running two dnclient services on a host at the same time.
Experiment with advanced settings
You might now find yourself asking, “If we can have two Managed Nebula networks running on the same hosts simultaneously while we migrate from one to the other, what keeps us from running more than one all the time?” The answer is “nothing, really” and there are some cool things we can do with two networks, in fact.
-
You could set up a second network to experiment with some of the performance settings in the “Advanced” tab on host, lighthouse, and relay pages. By leaving the original network unchanged, you’ll have a safe fallback in case your changes don’t go quite the way you planned.
-
Or you can try out a different set of roles or firewall rules, and confirm that everything has the connectivity you expect before making the same changes on your primary network.
There are a few caveats when trying this out. Be sure to configure different interface names for the host in each network (tun.dev), or give them tags that configure them for you. There’s also a -name parameter to use when running a second dnclient, or we also have a docker image available which can be used multiple times on a host while you are testing things out.
Isolate management traffic
You can even keep multiple Managed Nebula networks running on your machines indefinitely. Consider breaking out your management traffic from your production traffic. This has a number of benefits:
- CPU usage of management traffic does not impact your standard network’s traffic
- Allows simpler firewall rules (the management network can use basic roles that only allow ssh access)
- Provides a reliable means of managing your network and prevents accidental lock-out from changes to your primary network
Try it out
To create a new Managed Nebula network in your account, visit the admin panel and in the sidebar choose Settings -> Networks (direct link), then hit the “Add” button in the top right of the page and fill out the form. Or use our REST API to create and manage networks.
If you don’t already have an account, sign up for 100 free hosts, no payment info required. Or if you need an even larger network, check our simple pricing plans.
What are some other ways you can think of to use multiple networks? We would love to hear from you.
Nebula, but easier
Take the hassle out of managing your private network with Defined Networking, built by the creators of Nebula.